BluBox Access Control
SIMPLIFIED SECURITY. POWERFUL CAPABILITIES.


Open IP access control hardware
- Authentic Mercury open hardware platform
- Plug and play IP access control
- Available in kits, panels or single boards
- 1, 2, 4, 8, 12, 16 portal configurations
- Door, turnstile and elevator solutions
- Optional integrated access and lock power
- POE Controllers for installations at the “edge”
- Software-only upgrade of any of the 20-plus Mercury-based security systems

Board swap M5 CASI conversions
- Escape the proprietary security hardware cage
- Smooth transition from proprietary CASI hardware to open platform BluBØX hardware
- Board replacement of CASI hardware without rewiring
- Substitution of CASI Picture Perfect software with BluSKY software to manage the new system
- Automatic Picture Perfect to BluSKY database conversion tool
- Picture Perfect to BluSKY configuration and monitoring tool to support system conversions occurring over a period of time
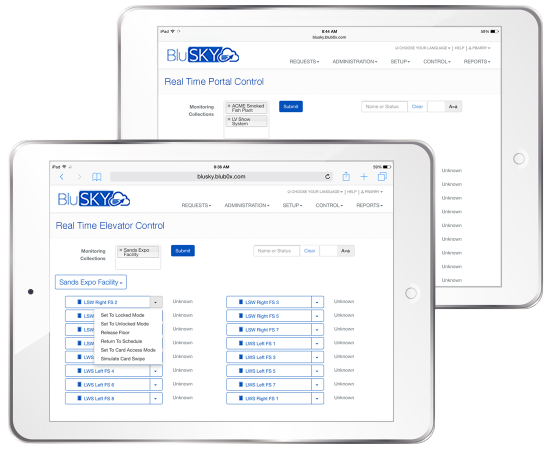
Web-based control and monitoring of portals and elevators from anywhere
- Real time single point or group status and control from any device, anywhere, anytime
- Perform lock, unlock, release, timed release, schedule, credential access and simulated swipe functions
- Provide Photo Verification of any portal
- View real time events
- Control a few portals in a single facility or thousands of portals across many facilities
- Control relay-based elevators
- Control elevator destination dispatch systems
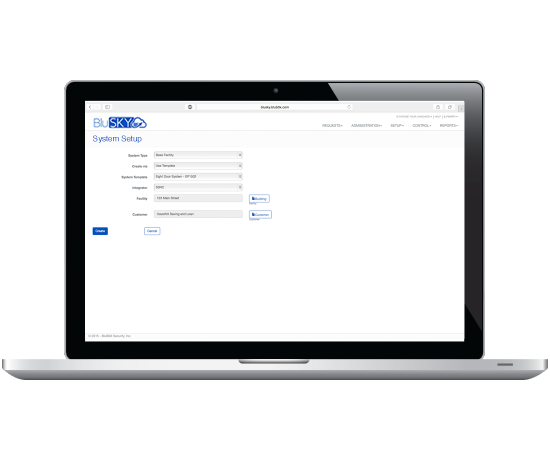
Flexible system creation tools
- Build a system component by component
- Copy from an existing system
- Copy from a predefined template
- Upload from spreadsheet
- Specify with parameters
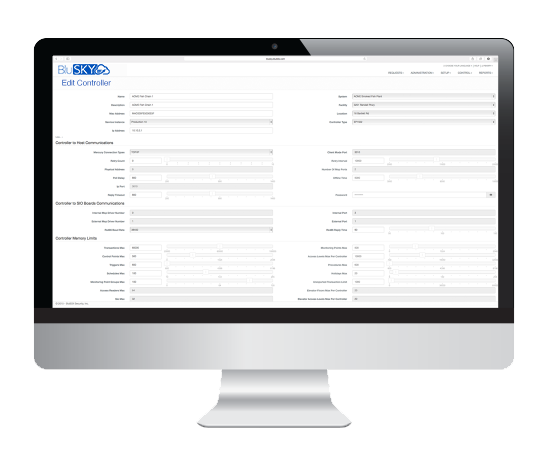
Dashboard-style configuration
- “At-a-Glance” view of important parameters
- Single-click access to configuration controls
- Configure from any device, anywhere, anytime
- Commission or troubleshoot at the security point with a smartphone or tablet
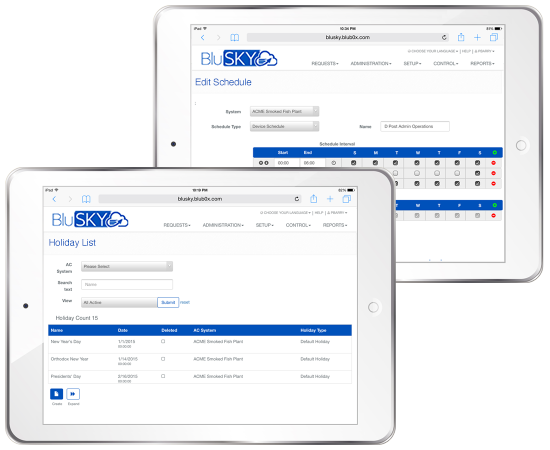
Predefined schedules and holidays
- Flexible schedule definitions
- Multiple intervals with up to one minute granularity
- Most commonly-used schedules are predefined
- Build custom schedules for those that aren’t predefined
- Most commonly-observed holidays are predefined
- Holiday dates automatically reloaded each year
- Select an access schedule for each holiday or globally apply one schedule
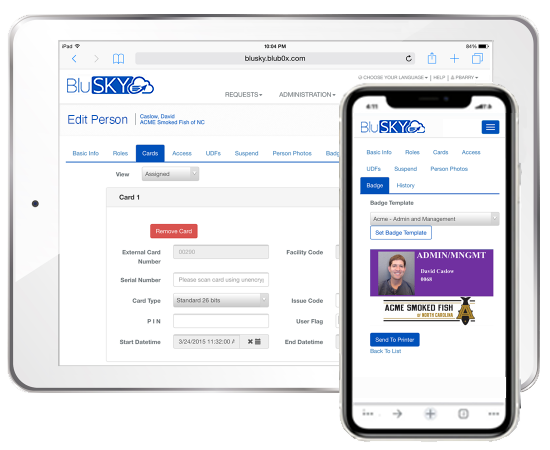
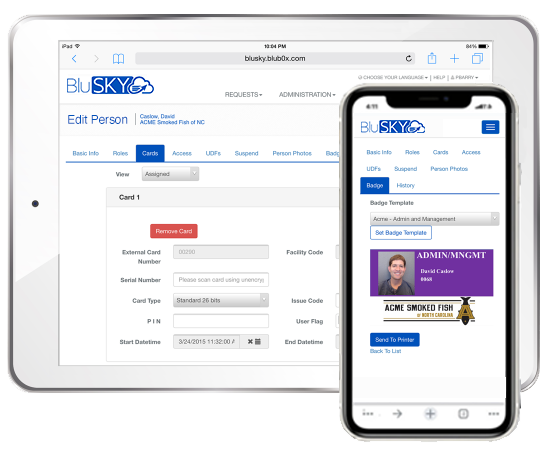
Simplified credential management
- Internal, external and card serial numbers are pre-loaded
- System provides four flexible methods to enroll a credential
- Includes integrated photo-ID badging with predefined badge templates and custom badge design tool
- Easily add and subtract credential attributes
- System shows all cards in use and all badge upload files for each customer
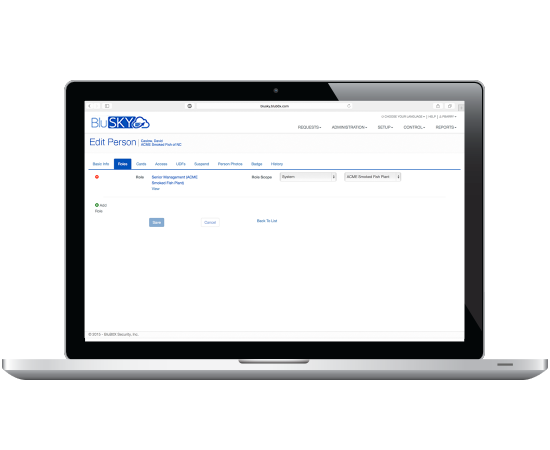
Role-based security management
- Predefined and custom role creation
- Single-click assignment of permissions, access rights, and badge templates
- Person based assignment of access rights and badge templates
- Automated role assignment for imported personnel records
Unified alarm, video, and visitor applications – everywhere
- One database, one user experience, all web-based applications
- Automatic association of alarm, video, and visitor data with every access event
- Integrated real-time control, monitoring and response
- Graphical map and locations user interface

Biometric Person Reader Management
- No biometric double data entry
- Each user can have multiple credentials
- Enroll at any Person Reader using a mobile device or computer
- Automatic verification of enrollment or de-enrollment
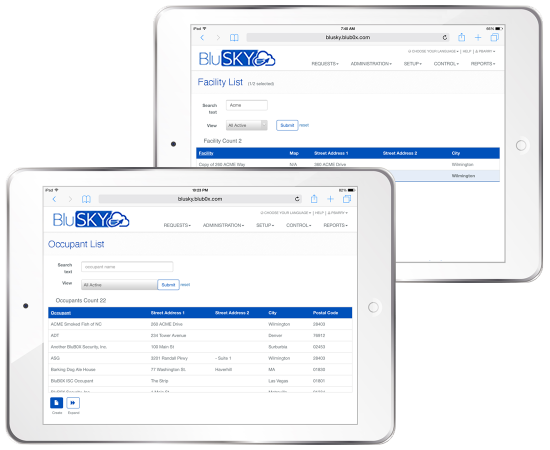
Multi-tenant and multi-facility administration
- The most efficient and secure way to manage multi-tenant and multi-facility physical security
- Manage all systems in all facilities from a single interface on any device, anywhere, anytime
- Tenants in a multi-tenant facility can manage their own company’s personnel databases, take pictures, issue credentials and run reports
- One personnel database can be used to drive both tenant security and base building security
- Eliminates double data entry and security loopholes
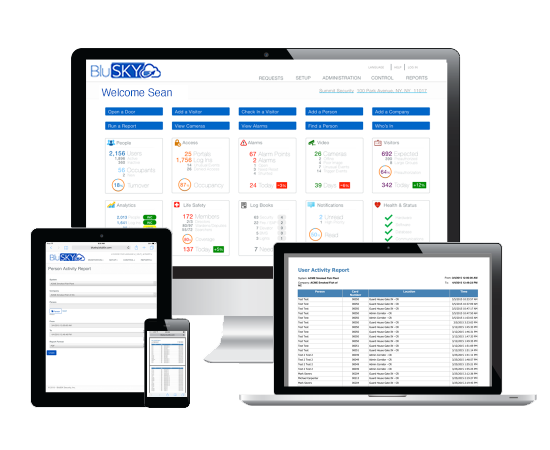
Access control reporting and analytics
- 15 standard access control reports
- Customizable input parameters
- Predefined and customizable dashlets and dashboards
- Subscription based report automation
- PDF and Excel output
- Many graphs and charts
- Provides key access analytics

Enterprise features.
- Advanced groups
- Global editing
- Global reporting and analytics
- Policy based access control
- Automated audits
- Credential inactivity
- Access rights
- Legacy system migration
